Category: Digital Marketing
-

Most Analytics Dashboards Fail. Will Yours?
-

Reimagining the Marketing Funnel: Time for a New Model
-

Analytics Storytelling: What Has Your Website Done for You Lately?
-

Cavalcade of 2023 Digital Marketing Predictions
-

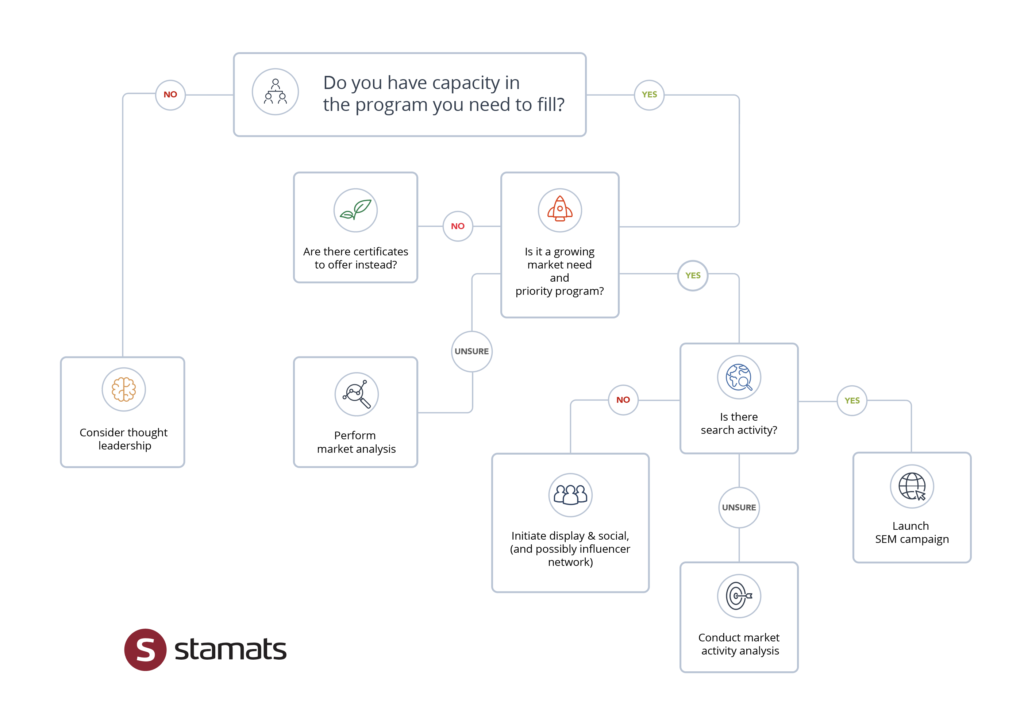
Program Decision Tree: A Tool to Select the Appropriate Digital Strategy
-

Google Business Profile Q & A
-

Community-First Content Tips from 6 Storytelling Experts
-

5 Strategies for Improved Audience Management
-

A Better Mousetrap: WebP Image Format and Why It Matters for your Website